According to British anthropologist Robin Dunbar, an individual's circles of friendship, or the number of stable relationships a person is able to maintain, have never exceeded 150 in any era. This is, remarkably, directly linked to biology. Research has shown that the size of the neocortex—which is responsible for higher cognitive functions, such as reasoning, planning, and social interaction—in the brain of primates is related to the size of their social groups. In humans, its size allows us to maintain social connections with approximately 150 individuals.
In practice, this phenomenon is consistently and clearly observable. For example, we tend to lend money to a relative rather than a neighbor from our apartment block. We're more inclined to share our knowledge with a friend than a stranger passing by on the street. We trust certain individuals while being suspicious of others. This also extends to our trust in government or banks at a personal level, where we rely on the enforcement of the regulations in place, though we can't always be sure of their effectiveness.
Building on the concept of trust circles in everyday life, cryptography has existed for thousands of years, initially serving to safeguard important information exclusively among these circles, excluding strangers from access to valuable data. However, today, cryptography addresses the opposite challenge by essentially making everyone, regardless of personal proximity, part of our trusted circle. This shift is crucial even for honest and decent individuals, given that cryptography underpins blockchain technology. Let's delve into its origins and understand its impact today.
The column of cortex/Wikimedia commons
Going Back in Time
Simply put, cryptography is the science of safeguarding information through encryption. The earliest instances of data encryption trace back to ancient Egypt. Around 1900 BCE, Egyptian scribes began to modify standard hieroglyphic symbols by altering their forms slightly: they added decorative elements and substituted some symbols with less familiar or obsolete ones. However, this ‘light’ encryption was not used to conceal information but to enhance the texts' esthetic appeal. These inscriptions adorned funerary objects, where the modified hieroglyphs were intended to draw attention.
Another early example of cryptography comes from one of the oldest civilizations, Mesopotamia. On a tablet dating back to 1500 BCE, an example of encrypted text was discovered—a recipe for highly sought-after ceramic glaze by craftsmen of that era. The encoder employed a simple substitution cipher, replacing one cuneiform symbol with another.

Hyroglifics texture on the wall inside Pharaoh ruins/Getty Images
The Simplest Cipher
Let’s try using the simplest encryption method. For example, let each letter in a word be replaced by the next one in the alphabet. After this transformation, the original text ‘My money is in the cupboard’ would look like ‘Nz npofz jt jo uif dvqfsve’. This type of encryption is known as a substitution cipher, and it can be used even in everyday situations. If it is agreed upon in advance, for example, it can be used as a means of secret communication in potentially dangerous situations.
The next cipher known to history belonged to Julius Caesar and was used in the Roman Empire. In this method, each letter in the text was replaced by the one that is three positions to the right. For example, A became D, B became E, and so on.
The encryption of letters was not done solely for governmental purposes but also for personal ones, as demonstrated in the ancient Indian text the Kama Sutra during the third to fourth centuries CE, which used a substitution cipher. Centuries later, during the French Revolution, when her life was in peril, the French queen Marie Antoinette employed a similar cipher in her love letters to Count Axel von Fersen. She sought to safeguard her personal correspondence amid the revolutionary turmoil that ultimately led to her execution in 1793.
As we have seen, encryption is a method of transforming ordinary text into a set of symbols that is unintelligible without a specific key for decryption. A key describes the method used to read and understand the text.
However, the effectiveness of any substitution cipher employed in Mesopotamia, the Roman Empire, and ancient India was challenged by the Arab philosopher and mathematician Al-Kindi. Born in the ninth century in what is now Iraq, Al-Kindi authored the seminal work Risalah fi Istikhraj al-Mu'amma (Treatise on Deciphering Cryptographic Messages). In this, Al-Kindi proposed analyzing the frequency of each letter in the encrypted message. By identifying the most frequent letter as ‘first’, the second most frequent as ‘second’, and so forth, Al-Kindi utilized the inherent patterns present in all languages. For instance, in Arabic, the most common letter is ﺍ (/aː/). This method enabled the hypothesis that the letter designated as first in the encrypted text could potentially correspond to ﺍ (/aː/).
It's fascinating how Al-Kindi was aware of the patterns in the Arabic language. During his time, local theologians were deeply engaged in studying hadiths, daily sayings attributed to Muhammad, and mostly aimed to authenticate each saying. To achieve this, theologians meticulously analyzed sentence structures and the origins of words, paying close attention to individual letters. Through their scrutiny, they discovered that certain letters appeared more frequently than others. Specifically, the letters ﺍ (/aː/) and ﻝ (/l/) were found to be the most common in Arabic.

Al-kindi cryptographic/Wikimedia Commons
Kabbalistic cryptography is an unusual and lesser-studied field that emerged in the Middle Ages. Kabbalah is a Jewish mystical tradition that began to systematically take shape as a doctrine in the twelfth century, although its roots extend much further back in history. It delves into the hidden aspects of the Torah, Talmud, and other sacred Jewish texts. Kabbalists were less focused on encrypting texts and more interested in ‘decoding’ them to uncover new meanings and secret connections. For this, they used methods such as assigning each Hebrew letter a specific numerical value, allowing letters to be substituted with corresponding numbers.
For a simple illustration of this method, let's create our own example. The word ‘shalom’ (meaning ‘peace’) consists of the letters Shin, Lamed, Vav, and Mem, and is written as שלום in Hebrew. The numerical values of each letter in the Jewish tradition are as follows: Shin (ש) = 300, Lamed (ל) = 30, Vav (ו) = 6, Mem (ם) = 40. Adding these values gives us: 300 + 30 + 6 + 40 = 376. This has the same numerical sum as the word ‘eshev’ (עשב), meaning ‘to sit’ or ‘to live’ (ע = 70 , ש = 300 , ב = 6). Such a coincidence can symbolize the idea that true peace is achieved when everyone finds their place or ‘sits’ in their place in the world. In reality, studying Kabbalah takes many years, and decoding real Kabbalistic texts is much more complex than this simple example we have examined. Nonetheless, it all stems from the idea that Jewish sacred texts contain multiple, from the literal to the profoundly mystical, levels of meaning and understanding. Accessing the ‘higher’ levels requires using numerical ciphers among other methods.
An engraving from Stefan Michelspacher's treatise Kabbalah: a Mirror of Art and Nature in Alchemy. 1615/Wikimedia Commons
Let’s take this story to another continent, South America, where the Inca Empire flourished before the arrival of the Europeans. Emerging in the thirteenth century, this civilization peaked between the fifteenth and sixteenth centuries, just before the Spanish conquistadors conquered the region. An integral part of Incan culture, as well as of the cultures that came before them, was the system of Quipu, which is made up of sets of colored strings with knots of various shapes and positions. The colors, types of knots, and their placement on the strings carried specific information.
There are theories that the Quipu system might have been used not only to record information but also to transmit messages that could be understood only by the initiated. Thus, if one invented their own rules, no one else could read the message using traditional methods. However, much of the knowledge about how to interpret Quipu was lost after the Spanish conquered the Inca. Today, scientists and researchers continue to work on deciphering this system.

Quipu system/Wikimedia Commons
During the Renaissance, cryptography reached a new level: encryption now occurred not manually but at a new level of complexity using special devices. One such device was the Alberti cipher disk designed by the scientist Leon Battista Alberti in the mid-fifteenth century. It consisted of two disks, each containing an alphabet. The outer disk was fixed, while the inner disk rotated. Each new position of the inner disk created a new encryption principle—in other words, a new variation of shifting the standard alphabet. This made it possible to change the key during operations, enhancing the cipher's complexity.
How the Alberti Cipher Disk Works
The Alberti cipher disk consists of two circular plates, and the letters of the alphabet are inscribed on both the outer and inner circles. The inner circle is smaller and can freely rotate relative to the outer one. Such a ‘machine’ can even be made at home using cardboard and wire.
To begin using it, choose the disk's initial position. In this case, you could align the letter A on the outer circle with the letter K on the inner circle. This is your encryption key.
Write your message on paper and using the disk, replace each letter of the message with the corresponding letter from the inner circle. Essentially, the disk speeds up encryption by visually indicating which letter should replace the original letter. For instance, if your message contains the letter A, where A on the outer circle aligns with K on the inner circle, then A is replaced with K.
To increase the complexity of the cipher, you can change the encryption key after a certain number of letters. For example, every ten letters, you could align the letter A on the outer circle with the letter L (or any other) on the inner circle, and so on.
Now the encrypted message can be sent to the recipient. To read it, the recipient must know the encryption key (the initial position of the disk). If you use multiple keys, and change the encryption method every ten letters, be sure to inform the recipient.

Alberti Ciper/Wikimedia Commons
Leonardo da Vinci's Mirror Writing
Around the same time as Leon Battista Alberti, his contemporary Leonardo da Vinci employed another original method of encrypting his own journal entries. He made many notes from right to left and mirrored the letters in such a way that the text could only be read using a mirror. In other words, da Vinci could write not just from right to left but he could reverse the standard orientation of letters. Instead of a conventional R, he would write Я and so on. This method became known as ‘mirror writing’. However, the exact reason why da Vinci made his notes in this manner remains unclear to science and history.

Leonardo Da Vinci. Codex On The Flight Of The Birds. Mirror writing. Rome/Getty Images
Polyalphabetic Ciphers
Leon Battista Alberti became one of the primary influences on the development of cryptography by introducing what became known as polyalphabetic encryption, where multiple keys are used simultaneously. In this method, the same letter of the alphabet can be encrypted in different ways, making deciphering a cipher much more challenging than with a simple substitution one.
Polyalphabetic encryption became the foundation for numerous subsequent systems, including the famous Vigenère cipher, which emerged a hundred years later. The French diplomat Blaise de Vigenère became central to this history by sheer accident. He acquainted himself with the works of past cryptographers and, in 1585, wrote his Treatise on Ciphers, describing the fundamentals of cryptography. Essentially, Vigenère combined previous approaches to text encryption without introducing anything new, but the cipher bore his name anyway. But it should be remembered that Blaise de Vigenère was no ordinary person. He was fascinated by chemistry, physics, astronomy, and mathematics. In Treatise on Ciphers, he first remarked: ‘Everything in the world is a cipher. All of nature is simply a cipher and secret writing.’
The Vigenère cipher operates in an ingeniously simple manner. Firstly, a keyword, such as for example BEE (or any other), is chosen. Then, a series of alphabets is used, each one shifted to the left, forming the Vigenère tableau:
1st row (heading): A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
2nd row: B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
3rd row: C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
4th row: D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
5th row: E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
6th row: F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
7th row: G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
8th row: H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
Let us consider that we want to encrypt the message ‘HELLO’ with the key ‘BEE’. We first repeat the key until it matches the length of the message. In this case, the key ‘BEE’ would repeat as ‘BEEBE’.
Now, let's proceed with encryption. Take the first letter of our message, H, and the first letter of our key, B. Find the row in the table starting with B. In this row, locate the symbol directly below the letter H in the header row. This symbol is I, which should replace H.

Blaise De Vigenere. 1595/Wikimedia Commons
This cipher was considered the best for approximately 300 years and was deemed unsolvable, meaning the message seemed impossible to decipher without knowing the key. It was often used in diplomatic and military circles, and it's clear why—it was relatively simple along with having a high degree of security. Its popularity crossed oceans; during the American Civil War in the nineteenth century, the Confederate Army, fighting to preserve slaveholding arrangements, used a version of the Vigenère cipher to encrypt their messages. Interestingly, throughout the war, the Confederacy primarily used just three keys: ‘Manchester Bluff’, ‘Complete Victory’, and, as the war neared its end, ‘Come Retribution’. And it didn’t have uses for only armies. The Vigenère cipher also inspired artists: Jules Verne incorporated a Vigenère-encrypted message into his novel The Begum's Fortune, challenging his characters to decipher it.
Meanwhile, various cryptographic methods continued to be used in Asia during this period. One example from the Qing dynasty (1644–1912) relates to cryptography used during the invasion of Western powers into China in the first half of the nineteenth century. Encryption methods could include well-known substitution ciphers and other principles including, for instance, changing the order of characters according to a rule known only to the sender and recipient or using a codebook where each word, phrase, or sentence corresponded to a unique code. All of these became especially important during the Opium Wars when foreigners began interfering in the affairs of the previously isolated empire.
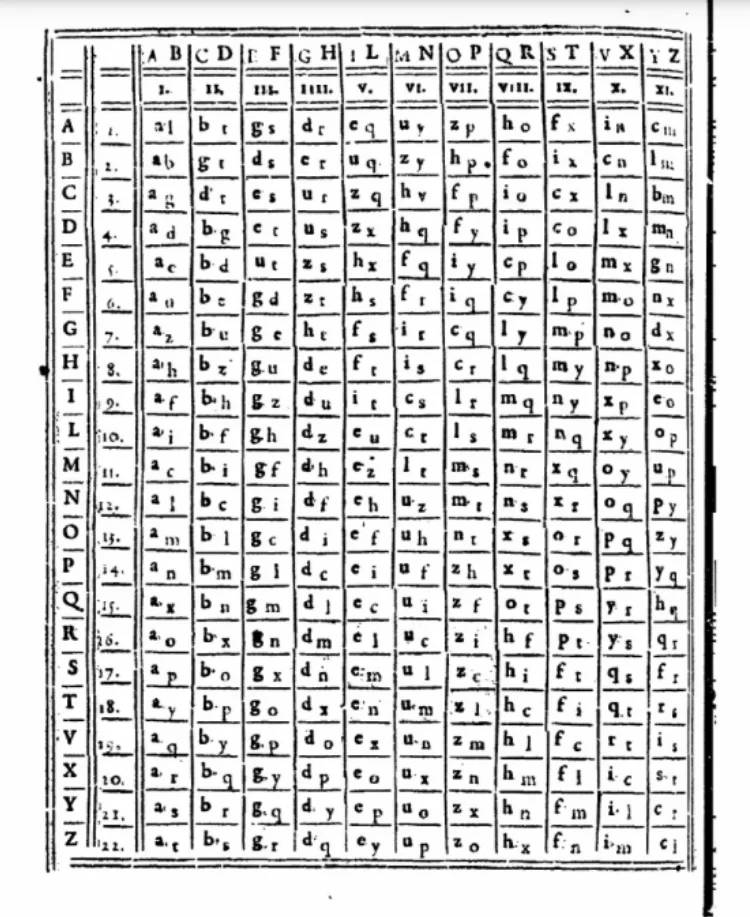
Blaise de Vigenère table in Latin alphabet//Wikimedia Commons
Learning to Decipher Ciphers
In the second half of the nineteenth century, a new era in cryptography began. The mathematician Charles Babbage in England and the cryptanalyst Friedrich Kasiski in Prussia independently developed methods to break the Vigenère cipher. These involved identifying the length of the key by detecting repeated fragments in the encrypted text followed by the process of deducing the actual key through statistical analysis.
Kasiski's method was something like this
According to the Vigenère method, to encrypt the message ‘HELLO’ with the key ‘BEE’, we first repeat the key to match the length of the message. In this case, the key ‘BEE’ would repeat as ‘BEEBE’.
Now, imagine you are looking at an already encrypted text and notice that the same sequence of letters repeats several times. This could indicate that the same part of the key was used at these points in the text. Therefore, the first step is to identify repetitions in the text.
Next, measure the distances between these repeated fragments. For instance, if the distance between repetitions is ten, it's possible that the length of the key is ten characters.
Then, examine the encrypted text and count each letter from 1 to 10 within each group separately. Simultaneously, make notes: list all the first letters of the encrypted text separately, then all the second letters, and so on.
Afterward, analyze each of these separately listed groups. Look at all the first letters: do you notice any particular letter appearing frequently? Compare this with the frequency of letters in Russian (or any other language you are working in). If the letter К (K) appears frequently in one of the groups, and in Russian, О (O) has a similar frequency, it might suggest that О was encrypted as К. Using this information, you can attempt to deduce some letters of the key and from there, speculate on the entire key.
Indeed, after such discoveries, code makers were pushed to devise new, more sophisticated encryption methods. Simultaneously, these breakthroughs introduced a significant amount of mathematics into the methods of breaking ciphers. Researchers began applying probability theory and statistical analysis to cryptography. Therefore, by the twentieth century, the development of cryptography became primarily accessible only to those who were highly proficient in mathematics.

Rune cipher resembling that found on the Kensington Runestone. Also includes runically-unrelated blackletter writing style and pigpen cipher. 1885/Wikimedia Commons
Developments in the Twentieth Century
Among the key features of the twentieth century are the world wars and global conflicts between nations. The First World War saw the widespread use of encryption across all fronts to safeguard military communications. This sparked an unprecedented surge in cryptanalysis as nations raced to crack enemy codes. Concurrently, fierce competition emerged in developing increasingly sophisticated and unbreakable encryption methods, fueling rapid advancements in both offensive and defensive cryptographic technologies.
In 1917, American engineer Gilbert Vernam proposed a method that was later known as the ‘one-time pad’ or Vernam cipher. This involved using a random key that could only be used once with the length of the key matching the length of the message. After that, the transformation of the message ‘HELLO’, for example, wasn't just through a simple table but via a binary system. Each letter or any other symbol from the original message was converted into a binary one using a specific, complex algorithm in this system. By the late 1940s, it was proven that this method was absolutely unbreakable. American mathematician Claude Shannon demonstrated that the cipher provides perfect secrecy only when the key is used once, is as long as the message, and is entirely random.
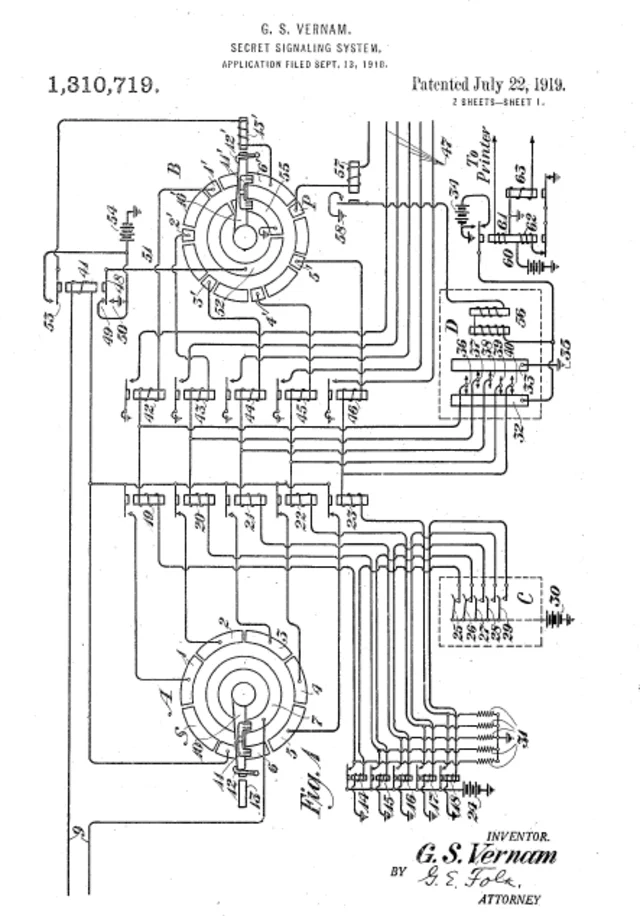
Patent for Vernum cipher/Wikimedia Commons
A parallel milestone of this time was the wide accessibility of electricity in the early twentieth century, leading to the emergence of not just mechanical but also electromechanical devices. Vernam thus created a device capable of encrypting messages independently, laying the foundation for ‘stream ciphering’, where both encryption and message transmission occur simultaneously.
However, in a situation where the message is a long one, a key like ‘BEE’ wouldn't suffice. Moreover, it's crucial that the key is used only once, and the message recipient must know it in advance. Sometimes, keys were transmitted using steganography, where the key was hidden within innocent-seeming illustrations or text. This made them seemingly visible to all but effectively hidden. Yet, the most reliable method was physically sending the key through spies or secret agents. Various techniques were devised, such as the ‘dead drop’. This was a predetermined location where one agent would leave information for another to retrieve later. Such locations could be anything from a hidden slit in a wall to a decoy dead rat that no passerby would care to inspect closely. The main advantage of a dead drop was its ability to keep surveillance communication during agent meetings.

Working on Enigma. 1944/Wikimedia Commons
Another famous example from the first half of the twentieth century was the cryptographic machine Enigma of the 1920s, used by the Nazi military during the Second World War. It was more straightforward than the Vernam cipher, lacking a unique one-time key, but it provided very secure encryption thanks to its special electromechanical system. This system combined mechanical and electrical elements: pressing a key on the keyboard triggered an electrical signal that passed through a series of rotating cipher disks, each altering the signal's path. The specifics of these alterations were known only to Enigma's manufacturers. Rather than a word or phrase, the key in this system was the machine’s configuration in a specific setting: users had to connect cables, set the disks in specific positions, and so forth. The German army distributed books with ‘keys’, detailing daily instructions on how to set up the Enigma each day for sending and receiving messages.
Shortly before the Nazi invasion of European countries in 1939, a Polish cryptographer deciphered the Enigma mechanism, a feat that couldn't have been achieved without complex mathematics. Marian Rejewski's discovery marked the beginning of decrypting German messages. He utilized a theorem that a mathematics professor later dubbed ‘the theorem that won the Second World War’.
Decrypting messages also required knowledge of the daily Enigma settings, and a challenge presented to mathematicians and their colleagues was trying to find these daily keys. Great minds once again delved into calculations, sharing their findings with British allies.
Ultimately, Alan Turing's breakthrough in this saga was the ‘bomb’, a device that accelerated the search for daily keys. The bomb simulated the operation of multiple Enigma machines and tested various combinations until coherent text emerged from the messages. Thus, the war marked the first instance of mass labor in cryptography. In Britain, approximately 200 bombs operated round the clock to intercept German messages.
The computer boom of the second half of the twentieth century obviously led to new complexities in encryption and decryption methods. Such highly sophisticated algorithms were created on computers that even a brilliant mathematician like Marian Rejewski would struggle to decipher them. Additionally, a new war emerged in the political realm—the Cold War. The secure transmission of information once again demanded a high level of secrecy. State agencies, such as the National Security Agency (NSA) of the USA, began investing heavily in advanced encryption systems. In the late 1970s, a breakthrough method emerged—public-key cryptography, specifically the concept of using two keys, invented by the Americans Whitfield Diffie and Martin Hellman.

Encryption device "Enigma"/Wikimedia Commons
Before this invention, any encryption method inherently included knowing how to decrypt the message. Diffie and Hellman proposed using one key for encryption and a completely different one for decryption.
The first key (public key) could be safely shared with anyone and could be likened to a lock, as it only encrypts the message. The second key (private key) remains secret and is used for decryption.
But why couldn’t the public key decrypt the message? We can understand this through a simple example of the wonders of mathematics. Suppose we want to encrypt the number 10 with our public key, which is 2. For encryption, a computer might use a simple multiplication operation: 10 × 2 = 20. The encrypted message is the number 20.
Now, let's try to decrypt it using the available public key 2. How can we do this if we don't know exactly which operation was used—it could be addition, division, or subtraction. We need to know precisely which operation was used for decryption.
Of course, this elementary example doesn't reflect the complex mathematical transformations that occur in a computer during public-key encryption. Nevertheless, it sheds light on the principle of what occurs.

Whitfield Diffie/Wikimedia Commons
Whitfield Diffie himself remarked on this breakthrough in 1992: ‘I understood the fundamental importance of public-key cryptography, but it all happened much faster than I expected. I didn't think that fifteen years after the discovery, they would become the foundation of advanced communication technologies, and indeed, thousands and thousands of such things are working in the world. I didn't expect that.’
Public-key cryptography also contributed to the development of the internet. Based on this foundation, technologies that secure the transmission of information over the web have emerged. For example, public-key encryption protects data from prying eyes when entering passwords or payment information on any website (albeit in conjunction with other modern information security methods).

M. Weik. The ENIAC Story. U.S. Army Photo. A technician changes a tube. Caption reads: Replacing a bad tube meant checking among ENIAC's 19,000 possibilities. Center: Glenn A. Beck/Wikimedia Commons
In Our Time
In the twenty-first century, the role of cryptography has undergone a huge paradigm shift. Rather than solely focusing on excluding outsiders, modern society now leverages cryptographic techniques to expand trust networks to include unfamiliar entities and organizations. This new approach relies on the impartial precision of mathematics—a discipline immune to bribery or manipulation. By creating specific mathematical algorithms, we can now establish systems where all participants enjoy unprecedented levels of security and trust, regardless of their familiarity with one another.
On 31 October 2008, a watershed moment in digital finance occurred when an enigmatic figure using the pseudonym Satoshi Nakamoto distributed a document entitled ‘Bitcoin: A Peer-to-Peer Electronic Cash System’ to a select group of cryptography enthusiasts and experts. This paper outlined the revolutionary concept of bitcoin and detailed the technical framework for the world's first decentralized digital currency. Bitcoin's innovation lies in its ability to function without a central authority like a bank while still ensuring secure transactions for all users.

Who is Satoshi Nakamoto? Graffiti in Tel Aviv /Wikimedia Commons
Bitcoin, while revolutionary, builds on years of scientific work predating cryptocurrencies. Satoshi Nakamoto's brilliance lay in combining existing principles with original ideas, documenting this synthesis, and launching the resulting mechanism. At the core of his program lies cryptography, specifically blockchain technology, which is perhaps more important than bitcoin itself in the context of global history.
Blockchain is a database of any kind of data without any central apparatus, which is considered the main innovation. This became possible because blocks of information within the database are linked together through encryption. ‘Mining’ cryptocurrency—the very process—is an attempt to solve a cryptographic problem; if your computer succeeds first, you receive bitcoins as payment.
The word ‘payment’ here is not incidental. Miners perform work: instead of a bank, they verify all past transactions by solving a complex problem. Moreover, technically, one cannot solve the problem correctly without first verifying the security and authenticity of past transactions.

Blocks for Bitcoin mining/Wikimedia Commons
Since 2008, investigators and enthusiasts worldwide have been striving to decipher who is behind the pseudonym Satoshi Nakamoto. It could represent an individual or a team. The quest is fueled by more than mere curiosity. Cryptographic estimates suggest Nakamoto owns around one million bitcoins, worth tens of billions of dollars at current rates. This means about every twentieth bitcoin is in the hands of its creator, causing concerns that an unknown individual holds such significant power. However, there is no concrete evidence that this is indeed the case. Only speculations and theoretical calculations exist.
Bitcoins are obtained through mining or can be purchased with traditional currency as it is possible to acquire currency like euros or dollars. Satoshi Nakamoto encouraged this approach, stating: ‘It would be smart to get some bitcoins in case it catches on. If enough people think similarly, it becomes a self-fulfilling prophecy.’ His advice eventually gained traction. In the early weeks, Nakamoto supported the network alone using his computers as no one else joined. Now, however, a single Bitcoin costs around $70,000, validating his foresight and the system's success.

Bitcoin/Wikimedia Commons
Why Do We Need This?
While cryptocurrencies may not completely replace traditional money, they will certainly not disappear without a trace from history. Now, we can see that currency can exist ‘by itself’, without a central authority, without a specific management apparatus. The emergence of new bitcoin units secures transactions—all of this is ensured by the system itself and its participants, who execute a precise algorithm (and physically cannot act otherwise).
Blockchain, in turn, will make, and, in fact, already is making, breakthroughs in all areas where this technology can be applied. This includes any processes involving common resources like climate, water, plants, animals, and nature conservation. Blockchain can help in the honest and transparent monitoring of carbon dioxide emissions or other pollutants, political elections, and transparent operations of charitable organizations. Simply put, blockchain can reduce bureaucracy in any complex process.
Radical innovations initially encounter skepticism and resistance as integrating new technologies into existing systems is challenging. These technologies need time to mature and reach their full potential, and their impact on our world and its future remains speculative. It's intriguing to consider how Dunbar's number (the cognitive limit of stable social relationships) will interact with technologies that eliminate the need for direct communication or trust between individuals. In these new systems, all participants are effectively ‘brothers’, connected through the technology itself rather than personal relationships.

Binary code/Wikimedia Commons
